Embark on a journey to safeguard your digital life from the ever-looming cyber threats. In this guide, we will unravel the essential steps and practices to ensure your online security remains intact. From understanding the various cyber threats to implementing robust security measures, let's delve into the realm of digital defense.
Understanding Cyber Threats
Cyber threats are malicious activities aimed at disrupting, damaging, or gaining unauthorized access to computer systems, networks, or data. These threats come in various forms and can have severe consequences if not adequately addressed.
Common Types of Cyber Threats
- Malware: Software designed to harm or exploit a computer system or network.
- Phishing: Fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity.
- Ransomware: Malware that encrypts files and demands a ransom for decryption.
- Denial of Service (DoS) Attacks: Overwhelming a system with traffic to make it unavailable.
Consequences of Falling Victim to Cyber Threats
- Data Breaches: Exposing sensitive information such as personal details, financial records, or intellectual property.
- Financial Loss: Theft of funds through fraudulent activities or ransom payments.
- Reputation Damage: Loss of trust from customers, partners, or the public due to security incidents.
Recent High-Profile Cyber Attacks
- SolarWinds Cyberattack: A supply chain attack that compromised numerous government and private organizations.
- Colonial Pipeline Ransomware Attack: Disruption of fuel supply in the U.S. due to ransomware targeting a critical infrastructure company.
- WannaCry Ransomware Attack: Spread globally, affecting thousands of systems and causing significant financial losses.
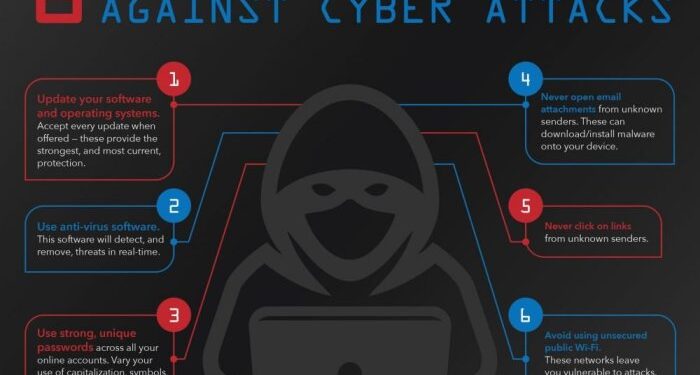
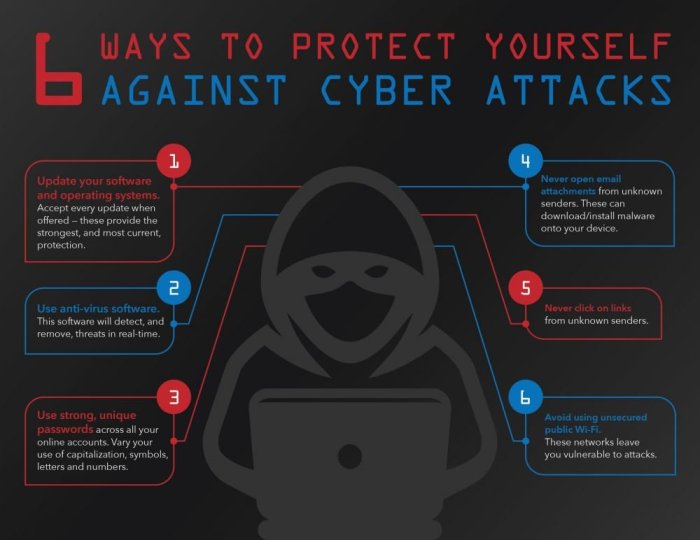
Strengthening Password Security
Ensuring strong password security is crucial in protecting your digital accounts and sensitive information from cyber threats. One of the first lines of defense against hackers is using strong and unique passwords.
Passwords are the keys to your online accounts, and using weak or easily guessable passwords can leave you vulnerable to cyber attacks. By creating strong, complex passwords, you can significantly reduce the risk of unauthorized access to your accounts.
The Importance of Using Strong, Unique Passwords
- Use a combination of uppercase and lowercase letters, numbers, and special characters to create a strong password.
- Avoid using common phrases, words, or personal information that can be easily guessed by hackers.
- Regularly update your passwords and avoid using the same password for multiple accounts.
- Consider using passphrase instead of a password for added security.
The Benefits of Using Password Managers
- Password managers help you generate and store complex passwords for each of your accounts securely.
- They can automatically fill in login credentials, saving you time and reducing the risk of phishing attacks.
- Password managers encrypt your password database, adding an extra layer of security to your accounts.
- Some password managers offer features like two-factor authentication for additional protection.
Tips for Creating Secure Passwords
- Choose passwords that are at least 12-16 characters long to make them harder to crack.
- Avoid using dictionary words or sequential numbers in your passwords.
- Consider using a random password generator to create unique and complex passwords.
- Enable multi-factor authentication whenever possible to add an extra layer of security to your accounts.
Implementing Two-Factor Authentication
Two-factor authentication (2FA) is an extra layer of security that requires not only a password and username but also something that only the user has on them, such as a piece of information only they should know or have immediately at hand - like a physical token or a smartphone.
Popular Platforms Offering Two-Factor Authentication
- Google: Provides 2FA through Google Authenticator or SMS verification.
- Facebook: Allows users to set up 2FA using authentication apps or text messages.
- Apple: Offers 2FA for Apple ID using trusted devices.
- Microsoft: Enables 2FA through the Microsoft Authenticator app or phone verification.
Setting Up Two-Factor Authentication
- Go to your account settings on the platform you want to enable 2FA.
- Locate the security or privacy settings and find the option for two-factor authentication.
- Choose the method you prefer for receiving verification codes (app, text, email).
- Follow the instructions to link your account to the authentication method.
- Verify that 2FA is working by logging out and logging back in with the additional verification step.
Keeping Software Updated
Ensuring that your software is regularly updated is crucial in protecting your digital life from cyber threats. Software updates often contain patches for security vulnerabilities that hackers can exploit to gain unauthorized access to your devices or data.
Significance of Updating Software
Regularly updating your software helps to close security gaps and prevent cyber attacks. Hackers are constantly developing new techniques to exploit vulnerabilities in software, so staying up to date with the latest patches is essential for keeping your devices secure.
Commonly Targeted Software
- Operating systems like Windows, macOS, and Linux
- Web browsers such as Google Chrome, Mozilla Firefox, and Safari
- Antivirus software and security tools
- Productivity software like Microsoft Office and Adobe Acrobat
Enabling Automatic Updates
Enabling automatic updates on your devices can help ensure that you are always running the latest software versions with the most up-to-date security patches. Here are methods for enabling automatic updates on various devices:
| Device | Method |
|---|---|
| Windows PC | Go to Settings > Update & Security > Windows Update and turn on automatic updates. |
| Mac | Open System Preferences > Software Update and check the box for automatic updates. |
| Android | Go to Settings > System > Advanced > System update and enable automatic updates. |
| iOS | Tap Settings > General > Software Update and turn on automatic updates. |
Securing Personal Devices
Securing personal devices such as smartphones, laptops, and other gadgets is crucial in protecting your sensitive information and maintaining privacy.
Enabling Device Encryption
Enabling device encryption adds an extra layer of security by scrambling data on your device, making it unreadable to unauthorized users.
- On iOS devices, go to Settings > Touch ID & Passcode and turn on Data Protection.
- For Android devices, navigate to Settings > Security > Encrypt Device.
- Ensure your laptop's hard drive is encrypted using built-in tools like BitLocker for Windows or FileVault for Mac.
Securing IoT Devices at Home
Securing Internet of Things (IoT) devices at home is essential to prevent hackers from accessing your network and compromising your privacy.
- Change default passwords on IoT devices and create strong, unique passwords.
- Regularly update firmware on IoT devices to patch security vulnerabilities.
- Enable two-factor authentication whenever possible to add an extra layer of protection.
- Keep IoT devices on a separate network from your main devices to limit access if one device is compromised.
Safeguarding Personal Data
Protecting personal data online is crucial to prevent identity theft, financial fraud, and privacy breaches. Here, we will discuss the risks associated with sharing personal information online, the concept of data privacy, and best practices for safeguarding personal data on social media platforms.
Risks of Sharing Personal Information Online
When you share personal information online, you are vulnerable to various risks, including:
- Identity theft: Cybercriminals can use your personal information to impersonate you and commit fraudulent activities.
- Financial fraud: Your financial details can be compromised, leading to unauthorized transactions and monetary losses.
- Privacy breaches: Your personal data can be exposed, leading to invasion of privacy and potential harm.
Data Privacy and Its Importance
Data privacy refers to the protection of personal information from unauthorized access or disclosure. It is essential because:
- Preserves confidentiality: Ensures that your personal information remains private and secure.
- Builds trust: Maintains trust with individuals and organizations that handle your data.
- Compliance with regulations: Helps adhere to data protection laws and regulations to avoid legal consequences.
Best Practices for Protecting Personal Data on Social Media
When using social media platforms, follow these best practices to safeguard your personal data:
- Review privacy settings: Regularly check and adjust your privacy settings to control who can view your information.
- Avoid oversharing: Be cautious about sharing sensitive details like your address, phone number, or financial information.
- Use strong passwords: Create strong and unique passwords for your social media accounts to prevent unauthorized access.
- Beware of phishing scams: Be wary of suspicious messages or links that may lead to phishing attacks aimed at stealing your data.
- Enable two-factor authentication: Add an extra layer of security by enabling two-factor authentication for your social media accounts.
Educating Yourself and Others
It is crucial to stay informed about cybersecurity threats and best practices to protect your digital life. Educating yourself and others about cybersecurity awareness can help prevent data breaches and cyber attacks.
Importance of Cybersecurity Awareness
Having a basic understanding of cybersecurity threats and how to mitigate them is essential in today's digital age. Cyber attacks are becoming more sophisticated, and being aware of potential risks can help individuals and businesses stay one step ahead of cybercriminals.
- Regularly updating your knowledge about the latest cyber threats can help you recognize phishing emails, malware, and other malicious activities.
- Being aware of cybersecurity best practices can help you protect your personal information and sensitive data from unauthorized access.
- Educating yourself about the importance of strong passwords, two-factor authentication, and software updates can significantly enhance your online security.
Resources for Staying Informed
There are several resources available online to help you stay informed about the latest cyber threats and security trends:
- Subscribe to cybersecurity blogs and newsletters from reputable sources such as Cybersecurity & Infrastructure Security Agency (CISA) and the Electronic Frontier Foundation (EFF).
- Follow cybersecurity experts on social media platforms like Twitter and LinkedIn to receive real-time updates on emerging threats and security tips.
- Attend cybersecurity webinars, workshops, and conferences to deepen your knowledge and network with other cybersecurity professionals.
Educating Family and Friends
It is equally important to educate your family members and friends about cybersecurity practices to create a safer online environment for everyone:
- Have open discussions about cybersecurity risks and teach them how to recognize common online threats.
- Show them how to secure their devices, use strong passwords, and enable two-factor authentication on their accounts.
- Encourage them to stay vigilant while browsing the internet and avoid clicking on suspicious links or downloading unknown attachments.
Backing Up Data
Backing up data is crucial in protecting your information from cyber threats. It ensures that even if your data is compromised, you have a secure copy to restore from. This can save you from significant losses and prevent data breaches.
Different Methods for Backing Up Data
- Cloud Storage: Utilizing cloud services like Google Drive, Dropbox, or iCloud allows you to store your data securely off-site, accessible from anywhere with an internet connection.
- External Hard Drives: Keeping backups on physical devices like external hard drives provides an additional layer of security, especially for large files and sensitive information.
Creating a Backup Schedule and Ensuring Data Recovery
- Set up a regular backup schedule: Establish a routine for backing up your data, whether it's daily, weekly, or monthly, depending on your needs and the frequency of changes to your files.
- Verify your backups: Periodically check your backup files to ensure they are intact and can be easily restored in case of a cyber attack or data loss event.
- Implement multiple backups: Consider creating multiple copies of your data in different locations to prevent a single point of failure and increase your chances of recovering your information.
- Encrypt your backups: Protect your backup files with encryption to safeguard them from unauthorized access, adding an extra layer of security to your data.
Outcome Summary
As we conclude this discussion on securing your digital life from cyber threats, remember that vigilance and proactive measures are key. By staying informed, adopting best practices, and educating others, you can fortify your online presence and navigate the digital landscape with confidence.
FAQ Explained
How often should I update my passwords?
It is recommended to update your passwords every 3-6 months to enhance security.
What is the best way to secure IoT devices at home?
Ensure your IoT devices are running the latest firmware updates, change default passwords, and set up a separate network for IoT devices.
Why is cybersecurity awareness important for individuals?
Cybersecurity awareness helps individuals recognize potential threats, avoid scams, and protect their personal information from being compromised.